The monitoring and capturing of all data packets as they flow through a network is known as ‘sniffing’. Network and systems engineers utilize sniffers to collect real-time network information. Network packets carrying private information, such as credentials and account details, are captured by attackers utilizing sniffers. Sniffers may indeed be installed, whether hardware or software, in the system. A malicious cybercriminal can capture and analyze all network traffic by deploying a sniffer in real-time on a network. The network interface by which a software sniffer sends all network traffic is configured.
A network will have a hardware packet sniffer connected to it. Then they are examined. A hardware packet sniffer logs the collected data for later analysis or transmits the collected packets to a collector.
As your data travels by, anyone who is packet-sniffing is able to do the following:
1. Go through each of your email.
2. View each of your passwords.
3. Know each website you have visited.
4. View every image from the websites you have visited.
5. Collect detailed account information (banking, credit card).
Data thefts, known as sniffing attacks, come whenever packet sniffers are being used to surreptitiously access and read sensitive data on a network. When the data packets travel via a computer network, they are collected. The methods or media used to execute this sniffing operation and capture the network data packets are simply called ‘packet sniffers’.
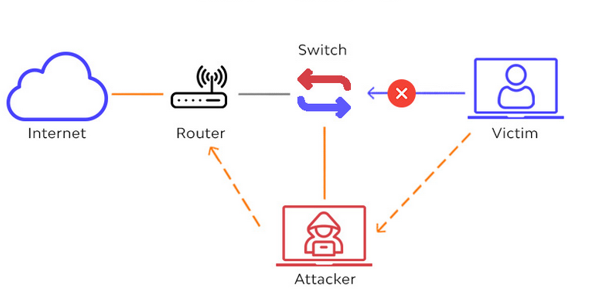
A sniffing attack is frequently alluded to as a ‘man-in-the-middle’ attack because it requires the machine gathering traffic to be situated between the communication systems in order to grab packets from a user (a ‘man-in-the-middle’ attack can also be waged on one of the two systems).
What is the concept of a ‘man-in-the-middle’ attack?
A ‘man-in-the-middle’ attack is a type of cyberattack during which the attacker sneakily hijacks and allocates messages between two parties who believe they are directly communicating with each other.
A type of eavesdropping is used in the attack, in which the attacker listens in on the conversation while seizing control of it.
You can equate any of this attack to the game of ‘telephone’, wherein one person’s comments are transferred from player to player, until they have altered by the time they reach the last person.
In a ‘man-in-the-middle’ attack, the third party intervenes in the communication without the knowledge of the other two participants and wants to control it to gain access to private information or to harm the other party.
‘Man-in-the-middle’ attacks:
1. are a form of session hijacking.
2. involve attackers placing themselves as proxies or relays in a continuous, authorized communication or data transmission.
3. allow intrusions to obtain private information.
4. enable the insertion of harmful links and data that can be used to steal information.
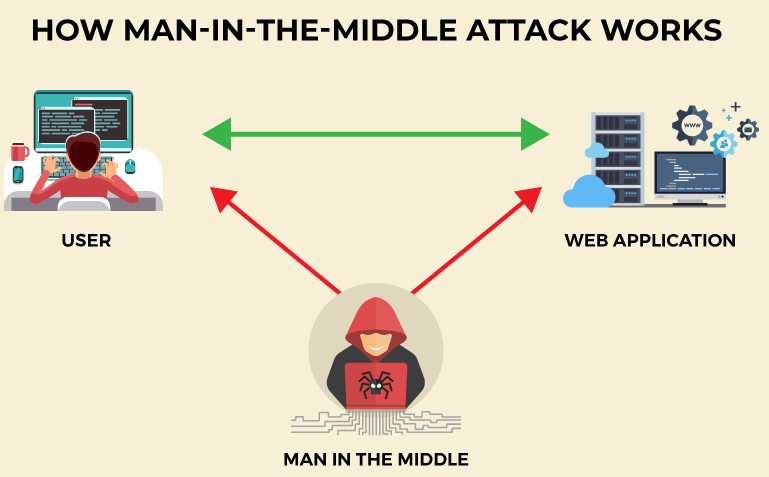
‘Man-in-the-middle’ attacks are only one form of session hijacking. Others include:
Sniffing: Data going to or from your device can be intercepted (or ‘sniffed’) by an attacker using software.
Sidejacking: If an attacker detects unencrypted login data, they can hijack a user session by sniffing data packets and stealing session cookies from your device.
The difference between Man-in-the Middle attack and sniffing
A sniffing assault violates someone’s privacy. It may be done through a switch’s span port, server procedures, or installing a device at an ISP to capture all incoming and outgoing traffic. However, sniffing is a passive MITM attack. If an attacker can gain access to any computers between your client and the server, they can use a sniffer to read the data while they are on the same network as you and listen to your communication (including your client and the server). A MITM approach is always a more active attack where the network path has been modified and include the adversary, such as a fraudulent access point or ARP/DNS poisoning, to allow sniffing, break encryption, and/or tamper with content delivery (an integrity and confidentiality attack).
A MITM can conduct sensitive operations based on the service accessed, hijack sessions, modify content to conceal behavior, inject malicious code, and hijack sessions once it has been identified as an active attack.
By
Narvesh Jaunky
IT Consultant and Microsoft Certified Trainer







![[Pénurie d’oignons rouges sur le marché] Kreepalloo Sunghoon : « La production locale est prévue pour août prochain »](https://sundaytimesmauritius.com/wp-content/uploads/2024/05/Oignons-rouges-218x150.jpg)
![[Conseillers du MSM] Cumul de postes sur les boards : Un système lucratif d’enrichissement personnel](https://sundaytimesmauritius.com/wp-content/uploads/2025/06/pic-2-150x150.jpg)
![[National Agency for Drug Control] Sam Lauthan : « C’est tous ensemble qu’on vaincra la mafia »](https://sundaytimesmauritius.com/wp-content/uploads/2025/06/WhatsApp-Image-2023-02-16-at-4.22.48-PM-e1738665704593-150x150.jpeg)
![[OMCA Foundation] Un dîner de gala pour soutenir l’accès aux soins des plus démunis](https://sundaytimesmauritius.com/wp-content/uploads/2025/06/f960dc68-ed3e-4619-ae8e-dd8f374d07c4-150x150.jpg)

![[Conseillers du MSM] Cumul de postes sur les boards : Un système lucratif d’enrichissement personnel](https://sundaytimesmauritius.com/wp-content/uploads/2025/06/pic-2-100x70.jpg)
![[National Agency for Drug Control] Sam Lauthan : « C’est tous ensemble qu’on vaincra la mafia »](https://sundaytimesmauritius.com/wp-content/uploads/2025/06/WhatsApp-Image-2023-02-16-at-4.22.48-PM-e1738665704593-100x70.jpeg)
![[OMCA Foundation] Un dîner de gala pour soutenir l’accès aux soins des plus démunis](https://sundaytimesmauritius.com/wp-content/uploads/2025/06/f960dc68-ed3e-4619-ae8e-dd8f374d07c4-100x70.jpg)